New Data Breach at IHG Hotels, and the List of Properties Involved (over 1100!)

InterContinental Hotels Group has announced that a data breach occurred at some of their franchise properties between September and December of 2016. Affected properties include brands Staybridge Suites, Holiday Inn, and Candlewood Suites.

The malware issue affects 1175 IHG properties spread across the United States, as well as some in Puerto Rico and Canada. Officials say that the breach occurred at properties that did not yet have a Secure Payment Solution (SPS) implemented yet, which is a point-to-point encryption payment acceptance solution.
Malware is bad stuff and IHG joins Hyatt, Omni, and Starwood in having had data breaches in the past year.
IHG reports that the security threat was right at front desks, rather than restaurant or retail outlets. A cyber security firm was brought in to do a full investigation upon discovery in February.
Information that may have been stolen –
Cardholder name, complete credit card number, expiration date, and security code.
Here’s a link to the page with all the properties affected by the breach.
There are so many properties where the breach occurred that you can search by state and city to find those you might have stayed at and the affected dates. Doing a search for just the properties in New York, NY the search came back with six properties.
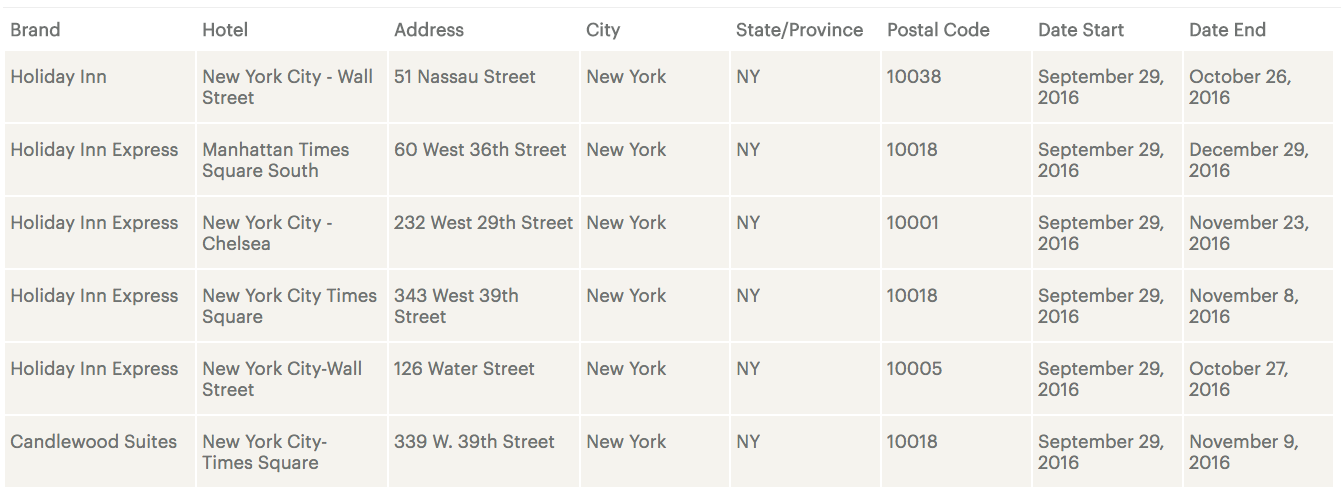
As always, guests are being asked to review their credit card statements and contact their bank or card issuer if there is something out of the ordinary spotted. IHG says that they are taking steps to “evaluate ways for franchisees to enhance security measures”.
I’ve said before that it seems to me that it would be a better idea to proactively modify systems to include the updated secure payment systems or stand-alone systems. When we hear about these malware issues, the companies involved have to call in a special team to investigate and then update their systems afterwards.
IHG identified the properties with malware issues as being those that hadn’t yet had the SPS implemented, so I’d be curious to know if IHG had already started implementing at other properties a few months prior and the scammers got ahold of the list of those not yet updated? Or maybe they hadn’t even started yet.
My best guest is that it is cost prohibitive to do the security updates, and the companies hope that there will be no issues until they have money set aside to be used (or are forced to update once there is a breach). It seems like every other month we hear about a new security breach.
I don’t know much about the security process though, and maybe the scammers change their methods slightly each time so it makes updates tricky.
Does anyone have an insider comment on why it doesn’t seem that these security updates are being done proactively?Â

One Comment